What is OTA (Over-The-Air)?
OTA (Over-The-Air) refers to the wireless distribution and installation of software, firmware, or configuration updates to devices over a network (Wi-Fi, mobile network, or satellite). It eliminates the need for physical connections like USB cables.
Where OTA is Commonly Used:
- Mobile devices (iOS and Android updates)
- IoT devices (firmware updates)
- Connected vehicles (car firmware updates)
- Smart home devices (e.g., smart lights, thermostats)
- Television and Set-Top Boxes (software updates)
Terminology Used in OTA
Here are some common terms related to OTA:
| Term | Definition |
|---|---|
| OTA Update | Wireless update of device software, firmware, or configuration. |
| Firmware | Low-level software that controls hardware components. |
| Bootloader | Initial code that runs before the OS and manages the OTA update process. |
| Delta Update | An incremental update that only downloads changed parts of the software. |
| Full Update | A complete package that replaces the existing firmware or software. |
| MDM (Mobile Device Management) | Tool used for deploying OTA updates in managed environments. |
| FOTA (Firmware Over-The-Air) | Wireless firmware updates for embedded systems or IoT devices. |
| SOTA (Software Over-The-Air) | Wireless updates for operating systems and software packages. |
| Push Notification | Alert to notify users that an OTA update is available. |
How OTA Works
OTA updates typically follow a structured process to ensure that updates are downloaded, verified, and installed safely.
Step-by-Step Process:
- Update Availability Check
The device periodically checks with the update server to see if a new version is available.- For smartphones, this check is automatic.
- For IoT devices, the manufacturer controls the timing and distribution.
- Update Notification
Users receive a notification (or MDM pushes it) that an update is available. - Download the Update Package
The update is downloaded wirelessly (Wi-Fi or cellular network).- Delta Update: Downloads only changed components (smaller size).
- Full Update: Downloads the entire package (larger size).
- Integrity Check
Once downloaded, the device verifies the update package to ensure it’s not corrupted or tampered with. - Installation
The update is installed in recovery mode or during a device reboot to prevent system instability.- Mobile devices and IoT systems often switch to a backup partition during the update.
- Dual-partition systems: The update installs in one partition while the device continues running, reducing downtime.
- Post-Installation Check
The device performs a self-check to confirm that the update was successful. - Reboot and Apply the Update
The device restarts and runs the new firmware/software.
Advantages of OTA
- Convenience: No need for cables or manual installation.
- Scalability: Updates can be pushed to thousands or millions of devices simultaneously.
- Security: Fixes security vulnerabilities quickly.
- Lower Costs: Reduces the need for physical recalls or technician visits.
Use Case Examples
- Mobile Devices: Android and iOS push regular OTA updates for OS enhancements and security fixes.
- IoT Devices: Smart devices like thermostats receive OTA updates to improve performance or add new features.
- Connected Cars: Tesla vehicles receive OTA updates for new software features and battery improvements.
- TV and Set-Top Boxes: Streaming devices like Roku update firmware to enhance compatibility and fix bugs.
Challenges of OTA
- Connectivity Issues: Poor network conditions can interrupt the update process.
- Security Risks: Unauthorized OTA updates could compromise the device if not properly verified.
- Storage Space: Devices with limited storage may struggle with large updates.
- Device Bricking: Failed or incomplete updates can render a device unusable.
Conclusion
OTA (Over-The-Air) is a crucial method for keeping devices up to date with minimal user intervention. It’s widely used in mobile, IoT, automotive, and smart home devices to ensure devices remain secure, stable, and feature-rich.
Here’s a step-by-step technical guide and architecture example for implementing OTA updates.
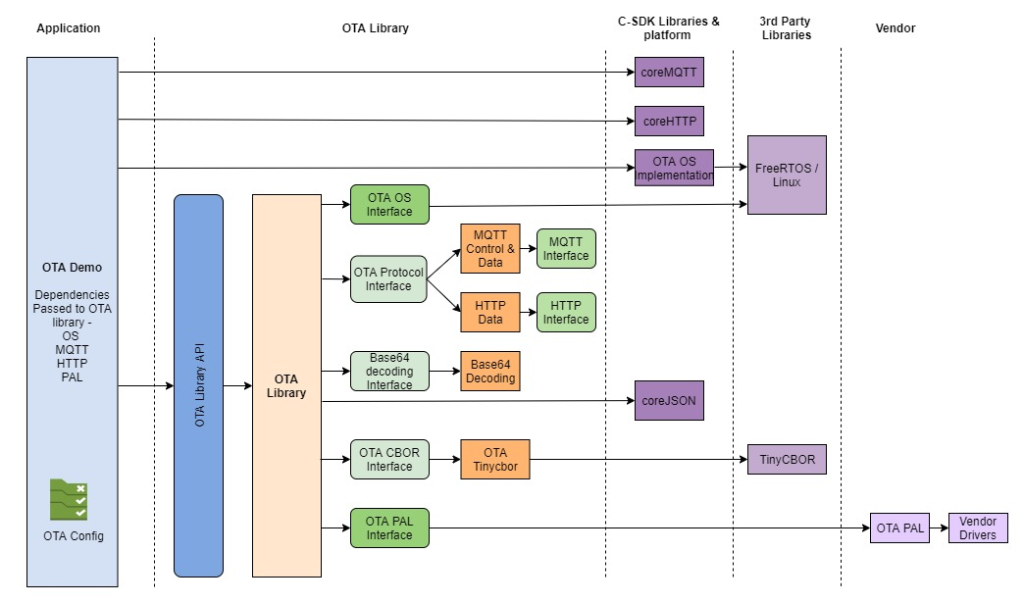
OTA Update Architecture
Key Components:
| Component | Function |
|---|---|
| Device | The target device receiving the update (IoT device, smartphone). |
| Update Server | Hosts the update package and manages distribution. |
| Notification Service | Notifies devices of available updates (push notifications). |
| Integrity Validator | Verifies the update package (checksum, signature verification). |
| Recovery/Installer | Applies the update safely without corrupting the system. |
Architecture Diagram
+---------------------+ +-------------------+
| Update Package | ---> | Update Server |
+---------------------+ +-------------------+
| |
v v
+----------------------------+ +----------------------------+
| Notification Service (Push) | | Device Requests Update Info |
+----------------------------+ +----------------------------+
| |
v v
+-----------------------------+ +-----------------------------+
| Target Device (IoT/Mobile)| | Integrity Check & Installer |
+-----------------------------+ +-----------------------------+
Step-by-Step Technical Guide for OTA Updates
1. Prepare the Update Package
Create an update package that contains:
- New software/firmware
- Metadata (version number, release notes)
- Digital signature for security validation
- Update type (Delta or Full update)
Example File Structure:
/update-package
├── firmware.bin
├── metadata.json
└── signature.sig
Metadata Example:
{
"version": "1.2.3",
"type": "delta",
"release_notes": "Bug fixes and performance improvements."
}
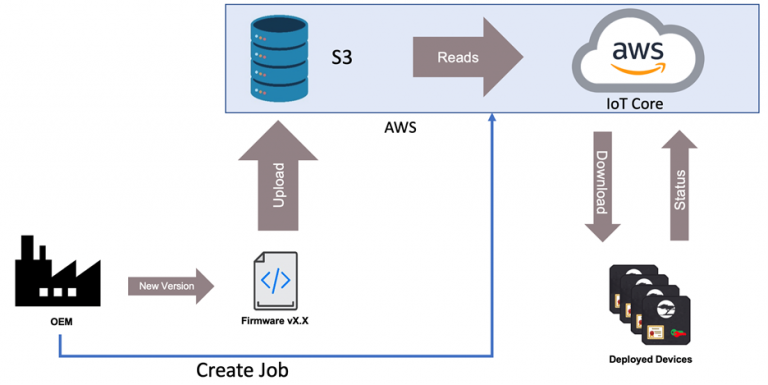
Code language: JSON / JSON with Comments (json)2. Host the Update on an Update Server
Deploy the update package to a cloud-based update server (e.g., AWS S3, Google Cloud Storage, or a custom server).
Example:
- Server URL:
https://updates.mydevice.com/firmware/1.2.3.bin - API Endpoint:
https://updates.mydevice.com/api/check-update
3. Notify the Device
Use a Notification Service to inform devices of a new update.
- Push Notifications (FCM/APNs) for smartphones
- MQTT or CoAP for IoT devices
- Polling Mechanism if push is not feasible
Example Notification:
{
"message": "New update available!",
"version": "1.2.3",
"url": "https://updates.mydevice.com/firmware/1.2.3.bin"
}
Code language: JSON / JSON with Comments (json)4. Device Requests Update
The device periodically checks for updates from the server or responds to a push notification.
Example HTTP Request:
GET https://updates.mydevice.com/api/check-update?device_id=12345
Code language: JavaScript (javascript)Response:
{
"version": "1.2.3",
"url": "https://updates.mydevice.com/firmware/1.2.3.bin",
"checksum": "abc123def456"
}
Code language: JSON / JSON with Comments (json)5. Download the Update
The device downloads the update package over a secure connection (HTTPS) to prevent tampering.
Best Practices:
- Use resumable downloads for large packages.
- Ensure download integrity using checksums (SHA256).
Example Checksum Validation (Python):
import hashlib
def verify_checksum(file_path, expected_checksum):
with open(file_path, "rb") as f:
file_hash = hashlib.sha256(f.read()).hexdigest()
return file_hash == expected_checksum
Code language: JavaScript (javascript)6. Verify the Update
Before applying the update:
- Check the checksum to ensure the file is not corrupted.
- Verify the digital signature to ensure authenticity.
7. Apply the Update
The device enters recovery mode or safe update mode to apply the update.
- For IoT Devices: Flash the new firmware to the device.
- For Mobile Devices: Replace system files or install the update package.
Example Firmware Update Flow for IoT Devices:
- Write the new firmware to a secondary partition.
- Switch the bootloader to the new partition.
- Reboot the device.
- Validate the new firmware.
- Roll back if validation fails.
8. Post-Update Verification
Once the update is applied:
- Perform a self-check to ensure the device is functioning properly.
- Report the update status to the server.
Example Update Status Report:
POST https://updates.mydevice.com/api/update-status
{
"device_id": "12345",
"version": "1.2.3",
"status": "success"
}
Code language: JavaScript (javascript)Security Best Practices
- Use HTTPS for all communication.
- Sign update packages with a private key and verify with a public key.
- Implement a rollback mechanism to restore the previous version if the update fails.
- Limit update retries to avoid bricking the device.
Example Use Case: OTA for IoT Devices
Device: Smart Thermostat
Update Type: Firmware Update
Process:
- The manufacturer releases a security patch.
- Devices receive a push notification to download the update.
- The firmware is downloaded, verified, and installed during off-peak hours.
- The device reboots and reports success to the update server.
Conclusion
OTA (Over-The-Air) updates ensure devices remain secure, stable, and feature-rich without requiring physical access. By following this architecture and step-by-step guide, you can build a reliable OTA update process for IoT, mobile, or embedded systems.
OTA Python Example Script
Here’s a sample Python script for an OTA update process that downloads a firmware update, verifies its integrity, and applies it to a target device.
Python OTA Update Example
import hashlib
import requests
import os
# Configuration
UPDATE_URL = "https://updates.mydevice.com/firmware/1.2.3.bin"
CHECKSUM = "abc123def4567890fedcba0987654321abcdef1234567890fedcba0987654321"
FIRMWARE_PATH = "/tmp/firmware.bin"
def download_firmware(url, destination):
"""Downloads the firmware update from the specified URL."""
print(f"Downloading firmware from {url}...")
response = requests.get(url, stream=True)
with open(destination, "wb") as file:
for chunk in response.iter_content(chunk_size=1024):
file.write(chunk)
print("Download complete.")
def verify_checksum(file_path, expected_checksum):
"""Verifies the checksum of the downloaded firmware."""
print("Verifying checksum...")
sha256 = hashlib.sha256()
with open(file_path, "rb") as file:
while chunk := file.read(4096):
sha256.update(chunk)
calculated_checksum = sha256.hexdigest()
if calculated_checksum == expected_checksum:
print("Checksum verification passed.")
return True
else:
print("Checksum verification failed.")
return False
def apply_firmware(file_path):
"""Simulates applying the firmware update."""
print(f"Applying firmware update from {file_path}...")
# Simulate the update process (e.g., flashing firmware)
os.remove(file_path)
print("Firmware update applied successfully.")
def main():
"""Main function to perform the OTA update process."""
try:
download_firmware(UPDATE_URL, FIRMWARE_PATH)
if verify_checksum(FIRMWARE_PATH, CHECKSUM):
apply_firmware(FIRMWARE_PATH)
else:
print("Update aborted due to checksum failure.")
except Exception as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
main()
Code language: PHP (php)How This Script Works:
- Download Firmware: Downloads the update from a specified URL.
- Verify Checksum: Ensures that the downloaded file matches the expected checksum to prevent corruption or tampering.
- Apply Firmware: Simulates the application of the firmware update (in a real scenario, this would involve flashing the device).
- Rollback on Failure: If checksum verification fails, the update is aborted.
Sample OTA Update Architecture Diagram