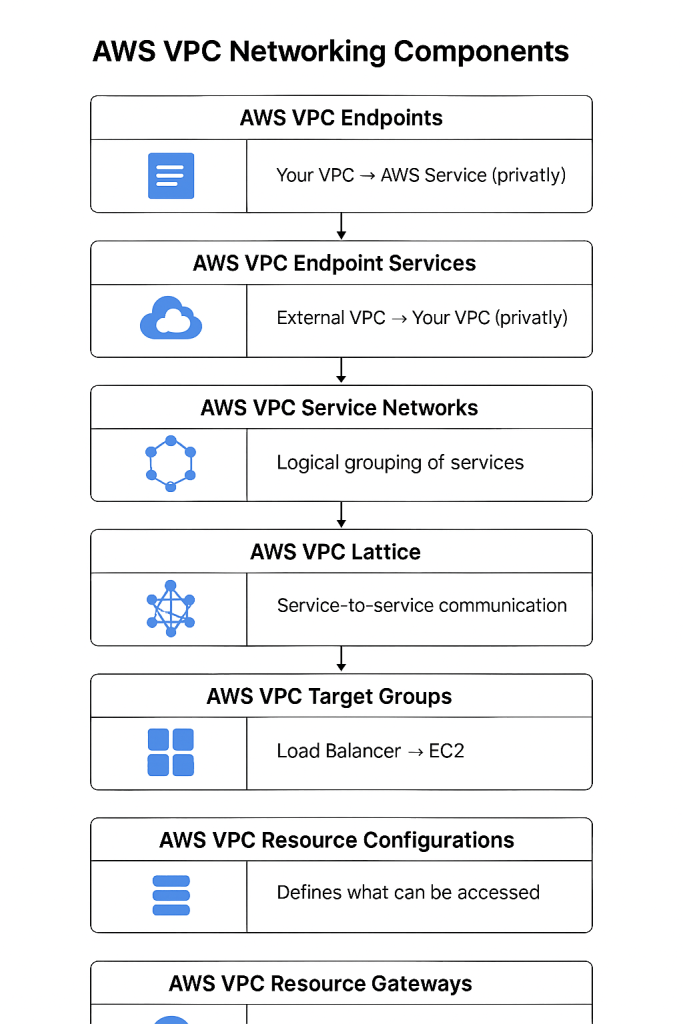
🧭 VPC Networking Scope
| Service | Traffic Type | Scope | Direction / Flow |
|---|---|---|---|
| VPC Endpoints | AWS Service Access | Internal VPC | Your VPC → AWS Service (privately) |
| VPC Endpoint Services | PrivateLink Service Sharing | Cross-VPC | External VPC → Your VPC (privately) |
| VPC Service Networks | Microservices Management | Cross-VPC / Multi-account | Logical grouping of services |
| VPC Lattice Services | App-level Service Mesh | Cross-VPC / Multi-account | VPC-A ↔ VPC-B services (via Lattice) |
| VPC Target Groups | Load Balancing Targets | Internal VPC | Load Balancer → EC2/Containers/Lambda |
| Resource Configurations | Shareable Resource Metadata | Your VPC | Defines what can be accessed |
| Resource Gateways | Access Point to Resources | Cross-VPC | External VPCs → Resource in your VPC |
Let’s break down these AWS networking concepts in a simple way, relating them to VPCs, the AWS network, and the public internet.
Understanding the Basics:
- VPC Network (Virtual Private Cloud Network): Think of this as your own private network within the AWS cloud. It’s like having your own isolated office building where you have full control over who comes in and out, and how the rooms (subnets) are organized. Resources within your VPC can communicate with each other privately.
- AWS Network: This is the entire infrastructure of Amazon Web Services. It’s like the whole city where your private office building (VPC) is located. The AWS network provides the underlying hardware and services that your VPC uses.
- Public Internet Network: This is the global network that everyone can access. It’s like the public roads and highways connecting different cities and buildings around the world.
Now, let’s explain the AWS networking concepts:
- AWS VPC Endpoints: Imagine your private office building (VPC) needs to access a specific service in the AWS city, like a storage warehouse (S3) or a database (DynamoDB). Instead of sending your traffic out onto the public internet roads, a VPC Endpoint creates a private, direct connection within the AWS network to that specific service. It’s like building a private tunnel directly from your office to the warehouse, so your deliveries don’t go out on the public roads.
- Example: Your application in a private subnet (a room in your office without direct internet access) needs to store files in Amazon S3. You create an S3 Gateway Endpoint, and your application can now access S3 privately without needing an internet gateway.
- AWS VPC Endpoint Services: This is like you offering a service from your private office building (VPC) to other companies (other AWS accounts or VPCs) in the AWS city. Instead of making your service public on the internet, you can use a VPC Endpoint Service to allow other companies to create a private connection directly to your service within the AWS network.
- Example: You have a custom application running in your VPC that other teams in your organization (in different VPCs) need to use. You can set up a VPC Endpoint Service, and those teams can create an Interface Endpoint in their VPCs to connect privately to your application.
- AWS VPC Service Networks: Think of this as creating a private intranet or a company-wide network that connects different office buildings (VPCs) within the AWS city. Services running in these different VPCs can then easily and securely discover and communicate with each other, as if they were all on the same network, without going over the public internet.
- Example: You have multiple microservices running in different EKS clusters across several VPCs. You can create a VPC Service Network, associate these VPCs with it, and your microservices can now communicate seamlessly and securely with each other.
- AWS VPC Lattice Services: Within a VPC Service Network (the company intranet), a VPC Lattice Service represents an individual application or microservice. It’s like a specific application or function available on the company intranet, like an internal HR system or a project management tool. You can define how this service listens for requests, how it routes traffic to the actual servers (targets), and who has permission to access it.
- Example: In your VPC Service Network, you have a “payment processing” service. You configure it with a listener for HTTPS traffic on port 443 and rules to route requests to a group of EC2 instances that handle payments.
- AWS VPC Target Groups: These are like teams or departments within a company that handle specific types of tasks. In the context of VPC Lattice Services, a Target Group is a collection of the actual compute resources (like EC2 instances, containers, or Lambda functions) that run your application or service. The VPC Lattice Service routes traffic to these target groups based on the rules you define.
- Example: Your “payment processing” VPC Lattice Service has a Target Group containing three EC2 instances that are actively processing payment requests.
- AWS VPC Resources Configurations: Imagine you have a resource in your private office building (VPC), like a database server, that you want to share privately with a partner company (another AWS account). A VPC Resource Configuration allows you to define this specific resource and the rules for accessing it, enabling the partner company to gain secure, private access without needing to know the details of your entire network.
- Example: You have an RDS database in your VPC that a partner needs to access for reporting. You create a VPC Resource Configuration for this database, specifying the port and the partner’s AWS account, allowing them to connect privately.
- AWS VPC Resource Gateways: This is like a dedicated reception desk in your office building (VPC) that handles all visitors (traffic) who have been granted access to specific shared resources via VPC Resource Configurations. It acts as the entry point into your VPC for this traffic.
- Example: When your partner tries to access the RDS database you shared, their traffic enters your VPC through the VPC Resource Gateway associated with that database’s Resource Configuration.
Interdependencies and Connections:
Here’s how some of these services are connected or interdependent:
- VPC Endpoints connect your VPC Network to specific AWS services or VPC Endpoint Services.
- VPC Endpoint Services are used by service providers to offer private access to their services running within a VPC Network. Service consumers then create VPC Endpoints to connect to these services.
- VPC Service Networks provide a logical boundary for VPC Lattice Services and VPC Resource Configurations.
- VPC Lattice Services define how traffic is routed to VPC Target Groups.
- VPC Resource Configurations must be associated with a VPC Resource Gateway to allow access to resources within a VPC Network.
- Clients can access VPC Resource Configurations directly via VPC Endpoints or through VPC Service Networks.
Use Cases Table:
| Feature | Use Case 1 | Use Case 2 | Use Case 3 | Use Case 4 | Use Case 5 |
| AWS VPC Endpoints | Private access to S3 from EC2 instances in a private subnet. | Securely connect to DynamoDB for database operations without internet access. | Access CloudWatch Logs privately for application logging. | Pull container images from ECR without public internet access. | Connect to KMS for encryption/decryption without traversing the public internet. |
| AWS VPC Endpoint Services | Offer a private API to other teams within your organization. | Provide secure access to a SaaS application hosted in your VPC. | Allow partner organizations to access specific resources in your VPC privately. | Create a centralized logging service accessible privately by multiple accounts. | Offer a secure data analytics platform accessible privately to different business units. |
| AWS VPC Service Networks | Connect microservices running in different EKS clusters across VPCs. | Enable secure communication between applications in separate AWS accounts. | Simplify networking for a multi-tier application distributed across multiple VPCs. | Create a shared environment for development and testing across different teams. | Facilitate secure data sharing and collaboration between different departments. |
| AWS VPC Lattice Services | Route traffic to different versions of an application for blue/green deployment. | Implement A/B testing by directing a percentage of traffic to a new feature. | Provide content-based routing based on URL paths or headers. | Secure internal APIs with IAM authentication and authorization. | Manage traffic to a group of Lambda functions serving a specific purpose. |
| AWS VPC Target Groups | Group EC2 instances running the same application for load balancing. | Define a set of IP addresses for backend services. | Register a Lambda function as a target for a service. | Include an internal ALB as a target for more complex routing within VPC Lattice. | Target specific Kubernetes Pods within an EKS cluster. |
| AWS VPC Resource Configurations | Share an RDS database privately with a partner AWS account. | Allow access to a specific internal IP address for a monitoring tool. | Provide secure access to a domain name pointing to an internal resource. | Share a group of related DNS endpoints with another VPC. | Grant access to a specific port range on an EC2 instance to a trusted entity. |
| AWS VPC Resource Gateways | Act as the entry point for traffic to a shared database resource. | Manage incoming connections to a shared internal application endpoint. | Control access to a shared service running on a specific IP address. | Provide a secure ingress point for a group of shared resources. | Serve as the single point of contact for all external access to resources in a specific VPC. |